Research Issues on Data Centric Security and Privacy Model for Intelligent Internet of Things based Healthcare
Introduction
Recently, as the information technology (IT) environment rapidly changes to the cloud, big data and Internet of things (IoT) era, there are necessity to take much thorough security management not only for storing data but also for encryption, movement, distribution and access of data. Intelligent IoT for healthcare applications has gained attention from vast research fields in recent years. The IoT connects all subjects and the healthcare system seamlessly, which requires secure data transmissions between entities regularly [1- 5]. IoT healthcare sector is resourceful and the important should be more focused on security, privacy and authentication. Thereby, data-centric security and privacy strategies are becoming a major research issue because of the variety of data that is generated by the IoT environment. Data-centric security is the key to establish policies that control the access rights of data and apply appropriate security technologies to the entire life cycle of data [6-7].
According to Hewlett-Packard analysis, 70% of IoT connected devices transmit data without applying any security measures, and 6 of 10 devices use vulnerable interfaces [8]. It has been shown that there are various security and privacy vulnerabilities in IoT. In particular, intelligent IoT has the advantage of making life convenient, but privacy issues can arise by recording and using personal private data. Biometric data such as an individual’s movement path, heart rate and blood pressure can be considered as highly sensitive privacy information. This paper aims to guide research issues and directions on data-centric security privacy model to overcome security and privacy limitations for realizing future intelligent IoT based healthcare service.
Discussion
IoT plays a vital role in healthcare applications. Healthcare applications should support clinical care, remote monitoring and context awareness. Furthermore, the risks of security and privacy should be removed during data collection from automatic medical data collection in the applications. There are already many researches to solve the issues [9-15]. However, they are not focused on data-centric security and privacy concerns, which are the core concerns on intelligent IoT based healthcare applications.
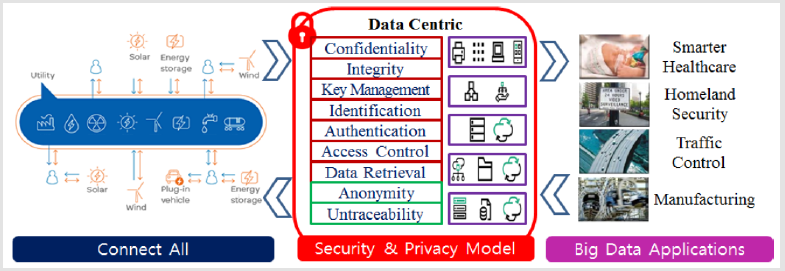
Intelligent IoT should be capable of collecting and sharing data from interconnecting billions and trillions of heterogeneous objects through Internet. The data privacy and security are the significant open issues in the intelligent IoT based healthcare applications. Especially, data privacy is crucial in the context of IoT based healthcare, which acquires data from IoT devices. Figure 1 shows a conceptual diagram of data-centric security and privacy model for intelligent IoT. To design a very effective and successful data-centric security and privacy model for healthcare applications, there are a lot of works to be done. We would like to suggest following some research issues and directions, which could be performed sequentially or separately.
Deriving Data-Centric IoT Features and Characteristics
It is necessary to define a data-centric security and privacy threat model by analyzing the various threat models and especially considering the intelligent IoT features and characteristics. It should be together with building testbed based on Arduino, Raspberry Pi, or any latest intelligent IoT devices to guild a prototype of a real experimental environment of the intelligent IoT based healthcare.
Developing Data Centric Security and Privacy Model: It is very difficult to maintain the security and privacy of data collected in the IoT environment and to control users with access rights from the collection phase to the consumption phase. In particular, since the intelligent IoT environment can integrate data that has not been aggregated at all, development of data-centric security and privacy model that considers intelligent IoT features and characteristics is a very important issue that has not yet been attempted.
Designing Data Centric Access Control Scheme: A new access control scheme should be developed based on attribute based encryption. The scheme should minimize sensitive data exposure through least privilege access and should provide privilege user control based on hierarchical key management technique.
Devising homomorphic encryption-based data retrieval technique: Secure and lightweight homomorphic encryption technique should be developed. That should provide data confidentiality and privacy while providing data-centric confidentiality and privacy.
Research on Data Centric Anonymity and Untraceability Techniques: In the intelligent IoT environment, lightweight techniques that can provide conditional anonymity and traceability. They should eliminate the per-session connectivity and suggest selective anonymity by considering the privileges of data users. In the upcoming eras, intelligent IoT based healthcare will be more and more applications because of its widespread adoption of IoT. Security and privacy provision should be the core part for the success of the intelligent IoT based healthcare applications.
Conclusion
Intelligent IoT based healthcare applications have been becoming an interesting field in the medical industry and research. However, the IoT healthcare is resourceful and the most important aspect is security and privacy. This paper gives a brief future research issues focused on data-centric security and privacy model for the intelligent IoT based healthcare applications. The contents would be useful for engineers, researchers, policy makers, health professionals and healthcare technicians for the better understanding of the contemporary research directions and issues.
Acknowledgement
This work was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2017R1D1A1B04032598).
More BJSTR Articles: https://biomedres01.blogspot.com/


No comments:
Post a Comment
Note: Only a member of this blog may post a comment.