Bioterrorism Information System as the Most Effective Tool in Management of Bioterrorism
Introduction
One of the most important types of terrorism is bioterrorism which involves illegal and deliberate use of biological agents, poisonous substances or chemical agents causing illness and mortality in humans, animals and plants. The purpose of such materials is to cause great damage while using a small amount of each one is very dangerous [1]. Application of the bioterrorism agents dates back to 1400 BC. Given the various events arisen from these agents, the history of their application can be divided into two periods. The first pertains to the era before the emergence of microbiology, the World War II, and before the 1925 Geneva Protocol. The blind use of biological agents by the users has been the main characteristic of this era [2]. The second period began from 1925 and lasted until the current time. The onset of this period coincides with the development of microbial genetics and other biological and biomolecular fields. This era resulted in the development of more dangerous biological agents through methods and techniques such as mutation and selection and protoplast fusion. The advancement of human knowledge in the genetics of microbes as well as the progress in aerobiology are other effective means in the modernization of biological weapons in this period [2-4].
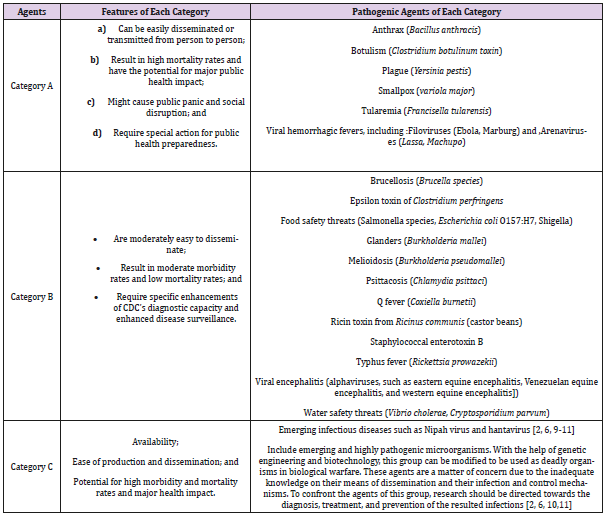
There are different lists of biological agents that can be used as a weapon in bioterrorism wars. These lists have been published by international organizations, research centers, and military experts. The most accepted classification of bioterrorism pathogens pertains to Centers for Disease Control and Prevention (CDC). Based on their hazards, this center categorized the pathogens into three groups [1,2,5-9]. Factors that contributed to this categorization include their profound impact on health, health fears, potential for re-dissemination, availability of protective vaccines or antimicrobial agents, proliferating pathogens, toxins or biomodulators, secondary transmission potential, and public health preparedness [2,5,7]. Each group has its own characteristics. The characteristics and the pathogens are classified and presented in Table 1. Considering the features presented and compared to chemical and nuclear weapons, biological weapons are more lethal, more powerful, less costly, easier to prepare, quitter, and deadlier. In addition, biological agents can be released through a variety of means [1,2,10-12]. According to specific features of biologic agents, their early detection is of great importance for their control.
The specific features of these agents include contagiousness (poisonous), ability to propagate through aerosols and hence covering a large area or the ability to infect water and food supplies ability to cause numerous fatalities, short incubation period and difficult diagnosis in the early stages stable and durable in environmental conditions and capable of retaining properties even after dissemination (especially in the aerosol form), and easy production and dissemination (especially in large quantities) [2,11,13]. Research results have shown that the Bioterrorism Information System (BIS) can systematically and continuously collect, analyse, interpret, and publish the data for early detection of outbreaks caused by bioterrorism. The system emphasizes identifying clinical symptoms based on patient behavior patterns and signs and symptoms from various references. The results of this system can be used in planning, implementation, and evaluation of public health performance to improve the management of bioterrorism events [1,2]. Timely response is another feature of this system, meaning that bioterrorism attacks are reported before the disease cluster is clinically identified [1,14,15].
According to CDC, BIS is the most effective means in the management of bioterrorism. Early detection and prompt response to bioterrorism attacks are one of the hallmarks of this system for reducing mortality [2,16]. In addition, other studies have indicated that implementation of a BIS system is effective in the management of bioterrorism events for the following reasons: collection of data that indicate the early stages of an outbreak, facilitating the identification of cases and case management, identifying and managing outbreaks, launching statistical warnings for users, providing continuous monitoring of the disease, analysing the exact process of the disease, providing timely and appropriate responses at the regional and local levels to facilitate the prevention and control of the outbreak at the national level, providing strong epidemiological information to assist in the long-term health management, planning, and policy-making [2,15-20]. Therefore, the effects of such a system depend on its features and abilities. The present study aimed to investigate the capabilities and features of BIS in effective management of bioterrorism events.
Background
Studies have indicated the importance of BIS in the management of bioterrorism events. BIS is capable of early detection of attacks and thereby can help effectively manage bioterrorism based on five technology groups including detection, communication, diagnosis and clinical management, surveillance, and supporting technology [2,21]. In addition, by introducing the key features of the BIS, studies consider this system as the core of effective management of bioterrorism events. The key features of the system are timeliness and rapid and early detection of the outbreak, high sensitivity and specificity, routine analysis of the data to facilitate decision-making and tracking the outbreak before the final diagnosis and laboratory approvals, using diverse and varied data sources, flexibility, rapid transfer and distribution of information [2,19,22]. Timeliness is critical in the bioterrorism events’ management given that the effective treatment of bioterrorism diseases is contingent on its timely identification. High sensitivity is important because the delay in identification of bioterrorism cases is regarded as a failure in its identification. In addition, a low specificity level leads to an increased number of false warnings entailing health costs [18- 20,22-24].
Research results have shown that BIS uses a variety of sources to increase accuracy [17]. These data resources are required for timely identification of bioterrorism events [25]. Integration of diverse data from various data resources provides the following advantages for managing bioterrorism events:
a) Simultaneous assessment of numerous health indicators.
b) Comparison of the aberrations to compare the trends of bioterrorism-induced illness.
c) Identification of confounding factors and reducing the system false warnings [2,18].
The results of various studies point out the capabilities and characteristics of BIS in effective management of bioterrorism events. For example, BIS employs the FSIS Automated Corporate Technology Suite (FACTS), which is an integrated information system, to reduce the data redundancy and increase the accuracy, completeness, and timeliness [1,2]. Moreover, BIS can also incorporate the Handheld Advanced Nucleic Acid Analyzer (HANAA) technology capable of identifying the biological agent in less than 30 minutes after the start of its dissemination. Therefore, such features can improve the BIS performance in the management of bioterrorism events [26].
Biological Defense Initiative (BDI) is another feature of this system. This is a national model for identification of bioterrorism events by integrating information from various detectors including BASIS, Portal Shield, RSVP, ESSENSE, and B-Safer [2]. By incorporating laboratory monitoring, the system performance is increased in the management of bioterrorism events. CDC has launched the Laboratory Response Network (LRN) to detect and identify biological agents. The laboratories of this network are categorized in four levels (A-D) according to their capabilities. The Level A laboratory has the minimum facilities to detect the suspicious samples using simple tests. This lab should send suspicious samples to a higher-level lab [2]. In this classification, based on biosafety levels (BL), the low-risk pathogens are placed at BL1 and the high-risk pathogens at BL4 [2,21]. This capability has increased the capacity of quick identification of RODS in the management of bioterrorism events [2,20]. BIS provides the appropriate threshold based on coding models, syndromic classification, risk prediction models, and strong base data. This feature is effective in reducing the errors in decision-making regarding the management of bioterrorism events [2,17].
For example, RODS use the syndromic classification based on Bayesian classifiers [27]. In addition, this system analyses the bioterrorism outbreaks information using warning detection algorithms and temporal and spatial statistical methods along with Natural Language Processing (NLP) [27-30]. This feature increases the analytical power of the system in the management process. According to studies on the use of communication networks, three requirements should be met to increase the power and capacity of the system in managing bioterrorism events: complying with the data transfer standards, the use of Internet-based communication infrastructures, and compliance with the agreements pertaining to the confidentiality principles when sharing information [2]. The BioWatch dashboard pertains to the information sharing and distribution technologies in BIS [31]. In addition, the use of charts, GIS, and LDAP protocols is mentioned in RODS and BioSense [28,32]. RODS use new software such as ArcIMS package and Map plot screen, which facilitates the update process and allows information to be displayed based on the time, region, and type of syndrome [28,30].
Reliance of the system on timely methods of distribution and display for generation of reports [33] allows rapid assessment of changes to identify the outbreaks quickly [22]. An example of this capability is the timely reporting of aberrations according to the Early Aberration Reporting System (EARS) [22,30]. Provision of option for users is another significant feature of the system. In this feature, users can determine and select a valid method for detecting the aberration and change and modify the threshold of warning sensitivity and specificity [22]. The use of various portals increases the system’s power in the distribution and display stages. For example, the ESSENCEII system provides four portals to the users to allow them view raw data and their processing results. These four portals include a map portal which presents the geographical distribution of the data, a warning list portal, a search portal, and a report summary portal [34].
Findings
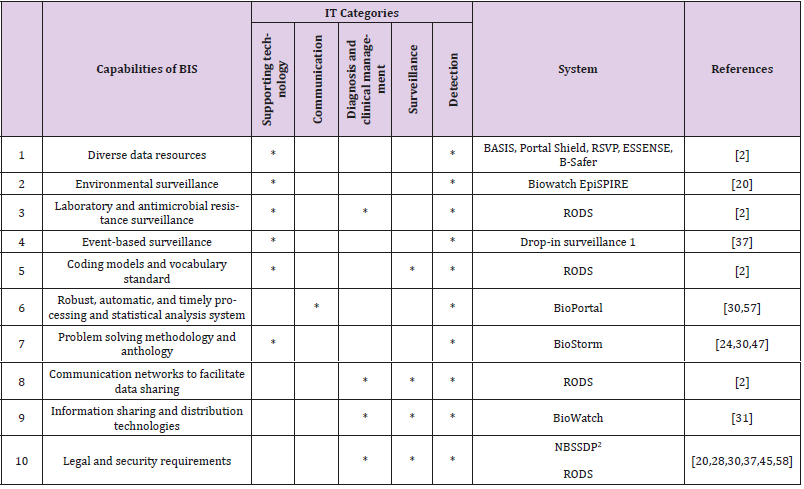
In general, the capabilities and characteristics of BIS which contributes to the effective management of relevant incidents can be divided into 10 categories [2,33,35-37].
Diverse Data Resources Relying on Superior Technologies
Types of data resources for the BIS are divided into five categories:
i) Data and evidence before the diagnosis of illness such as person’s behavior (absenteeism) and OTC sale [30]. These data are timely and non-specific (preclinical with low specificity percentage). An example of this model is the use of data related to the human behavior in the Bio Alert System developed by Defense Advanced Research Projects Agency (DARPA) [2,21]. In addition, the use of keywords on the Internet in Google to identify early outbreaks can also be included in this category [2,20].
ii) Laboratory symptom and orders which are timely and relatively specific (clinical or pre-diagnostic) [2,24].
iii) Final diagnosis of illnesses and results of tests, which though not timely, are specific with a high specificity [2,24].
iv) Data from biological detectors and biosensors that are both timely and have a high sensitivity and specificity [2]. Molecular Recognition-based Real Time Detection [21] and Epidemic Outbreak Surveillance (EOS) are two examples of this type. These systems are capable of an early identification of biological events according to DNA-based advanced technologies [2]
v) Data from security agencies based on the presence of a biological agent at a specific location and time [2].
Environmental Surveillance
In this system, continuous sampling reveals the presence of biological agents in various environments. Examples of these systems include remote identification systems such as radar and doppler radio as well as point detection systems such as EpiSPIRE and BioWatch [20].
Laboratory and Antimicrobial Resistance Surveillance
In this case, timely collection, analysis, and reporting of important antibiotic-resistant pathogens are carried out to identify biological agents [21]. Studies have shown that the sensitivity of these systems are 76-100% [23]. As a specific ability, it can identify unusual organisms such as anthrax, smallpox, and Ebola, as well as known and antibiotic-resistant organisms [38].
Event-Based Surveillance
Although many BISs continuously collect, analyse, and report data, some systems are intended for short-term use. These systems are known as event-based or drop-in systems [20] and are built following specific events such as Super Bowl. The bioterrorism syndromic surveillance system, which was created after September 11th, 2001 in New York for 30 days in 15 emergency units, is an example of this model [17,27,39].
Coding Models and Vocabulary Standard
BISs use classification systems in the form of four categories: classification systems, core vocabularies, cross reference ontology, and messaging standard in public health [30,37,40-42].
Robust, Automatic, and Timely Processing and Statistical Analysis System
This feature is based on Strong Outbreak Recognition Algorithms and robust, reliable, and flexible prospective and retrospective statistical methods for changing the threshold of sensitivity and specificity indices with respect to time and place [1,2,22,34,36,43-46].
Problem Solving Methodology and Anthology
BioStorm is the most prominent example of this system and a type of knowledge-based BIS [24,30]. Problem solving methods in this system are directed based on knowledge adjusted by anthology [24,30,47].
Communication Networks to Facilitate Data Sharing
BISs use communication networks to increase interoperability and provide accurate and timely reports [2]. The most common communication networks used in BISs are:
National Laboratory Response Network (NLRN): Aiming to establish a secure network for providing standard diagnostic protocols for bioterrorism laboratories [2,20,48].
Epidemic Information Exchange (Epi-X): Aiming to facilitate the secure communication between epidemiologists for rapid analysis and reporting [2,48-50].
CDC’s Health Alert Network (HAN): Aiming to facilitate communication and sending messages to health professionals [50]. This health alert network pertains to the provision of early warnings in response to bioterrorism events [2,21].
Public Health Information Network (PHIN): Aiming at proper and secure exchange of information related to BIS in five performance fields of identification, surveillance, data analysis, knowledge management, health warning, and response [37,51-53].
National Environmental Public Health Tracking Network (NEPHTN): The BIS pertaining to identification of environmental threats communicates with this network [2,21].
Information Sharing and Distribution Technologies: In this feature, spatial- and temporal-based information distribution technologies such as GIS, dashboard, and rapid and precise warning system are used [24,30,47] for the productivity of information distribution. Other BIS capabilities in this category include use of specific portals, automatic message sending system to inform specialists [54] and use of alert system for bioterrorism events in the form of the National Bioterrorism Security Advisory from severe threat (red) to mild threat (green) [1,2,55].
Legal and Security Requirements
Regarding legal requirements, the two following requirements can be pointed out:
a. Compliance with General Standards of ASTM, HL7, and ISO [49,53,56-58].
b. Compliance with the specific standards of BIS, such as Pandemic and All-Hazards Preparedness Act (PAHPA) [50] and Resolution 1540 of the United Nations Security Council, and compliance with security requirements and connection to security centers such as the FBI [20,28,30,37].
As its point of strength, BIS complies with the security requirements in the following five areas in the management of bioterrorism events: security management and policy making of BIS, system software security, security in the field of human resources, security in the field of equipment and hardware, security in the field of data collection and processing, and storage, transmission, and distribution of information [1,2]. Each BIS has specific features, each of which uses one or more technology groups that are effective in the three stages of management. All features discussed in the Table are effective with varying intensity and strength in three stages of prevention, response, and recovery in the bioterrorism events’ management (Table 2).
Table 2: Capabilities of BIS based on technology groups in the management of bioterrorism events.
1-. Drop-in bioterrorism surveillance system for World Series 2002in Phoenix, Arizona
2-National Bioterrorism Syndromic Surveillance Demonstration Program
Conclusion
BIS is considered as the main element in all stages of the bioterrorism events’ management, namely the prevention, response, and recovery stages. By designing and implementing the system based on the features and capabilities presented in this paper, the system will be able to play an active and effective role in the triple stages of bioterrorism events management. Focusing on management and technical features and abilities in all three stages will help manage the bioterrorism events effectively. Enhancing each of the BIS features will improve the system power in different stages of management. Finally, effective management of bioterrorism events will increase the social security and health.
Suggestions
a) It is suggested that various data sources be used in designing the National Bioterrorism Information System. Equipping the system with biological detectors and biosensors as well as using information related to the threats of bioterrorism attacks obtained from intelligence and security organizations have led to a real-time and accurate detection of bioterrorism outbreaks.
b) It is recommended that coding systems and national vocabulary systems be used for every region for an accurate and real-time bioterrorism outbreak detection.
c) It is suggested that localization in the classification of biological agents based on the demographic and epidemiological features of a country for National Bioterrorism Information System be considered.
d) It is recommended that policy and security priorities based on environmental surveillance, Laboratory and antimicrobial resistance surveillance and event-based surveillance be considered in strategy selection for system performance.
e) It is recommended that flexible and advanced statistical methods be used at data processing phase. Geographic features of the region, demographic characteristics, classified system selection, epidemic diseases, determination of syndrome groups, and attention to the season and time of the event are significant points in order to determine threshold in data processing phase.
f) It is suggested that security policies of each country, the extent and the impact of the bioterrorism event be considered for information sharing and distribution technologies in National Bioterrorism Information System.
Competing interests: The authors declare that they have no competing interests.
More BJSTR Articles: https://biomedres01.blogspot.com/


No comments:
Post a Comment
Note: Only a member of this blog may post a comment.